302 Redirect
Insecure connections⌗
SIGNAL⌗
On 3/17/2021, The Case Worker sent me the following screenshot:
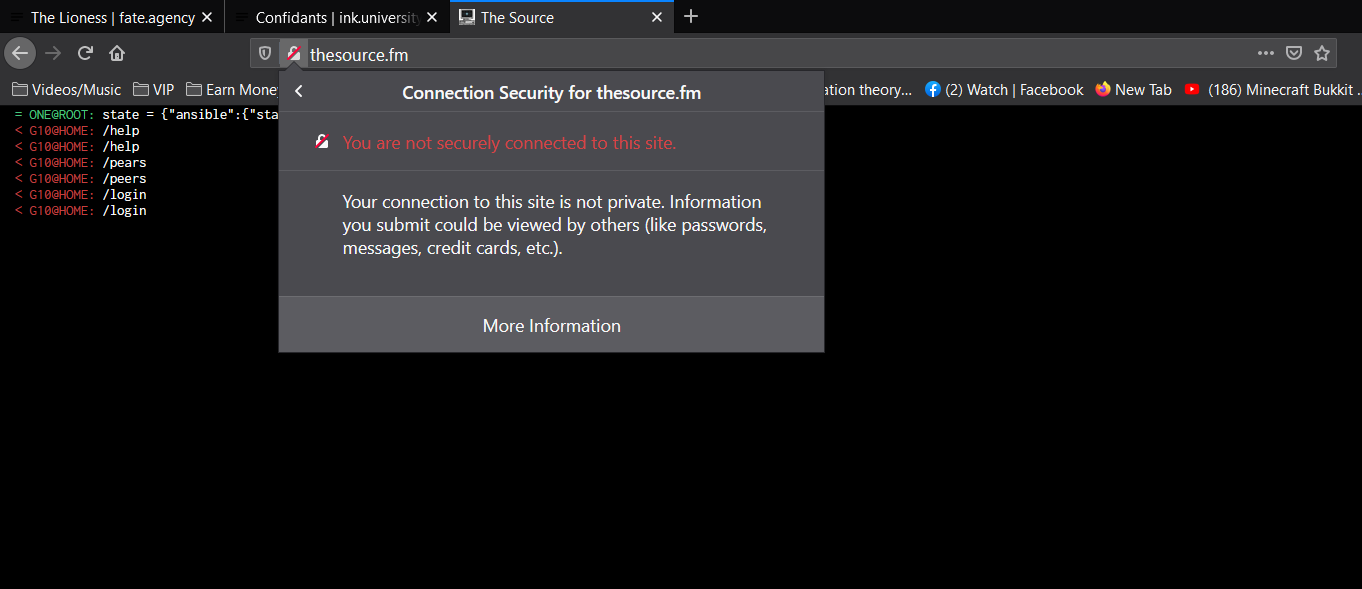
ANALYSIS⌗
Until this point, I hadn’t noticed that Cloudflare’s IPFS gateway did not automatically redirect HTTP connections to HTTPS. That was bad; it means that a malicious actor may be able to snoop on visitors, or even manipulate content!
It appeared as though HTTPS redirection could be enabled for end-to-end encrypted communications. However, this feature requires DNSSEC, which isn’t available for .fm domains.
Thus, I had no good option for redirecting this site to HTTPS.
ACTION⌗
In response, I implemented passive redirection via some Javascript. This isn’t great, because the initial connection is still unencrypted, and thus, can be manipulated. But, it’s better than nothing.
You can see remnants of that code here.
ANALYSIS⌗
Trying to implement this ended up being more trouble that it was worth. This type of redirection breaks IPFS sites. Thus, I disabled redirection entirely.
SIGNAL⌗
Just a few days later, Cloudflare’s IPFS gateway was configured to redirect my website to HTTPS - with no passive redirect configured at all!
ANALYSIS⌗
I strongly suspect that someone was watching. And they fixed my problem with a server-side redirect (which is the best way to do this.)